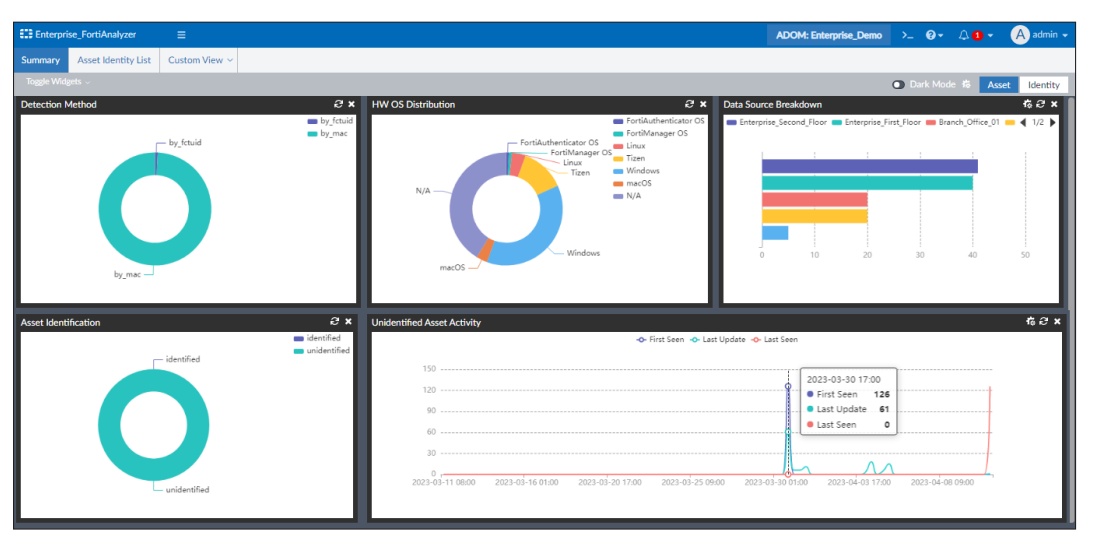
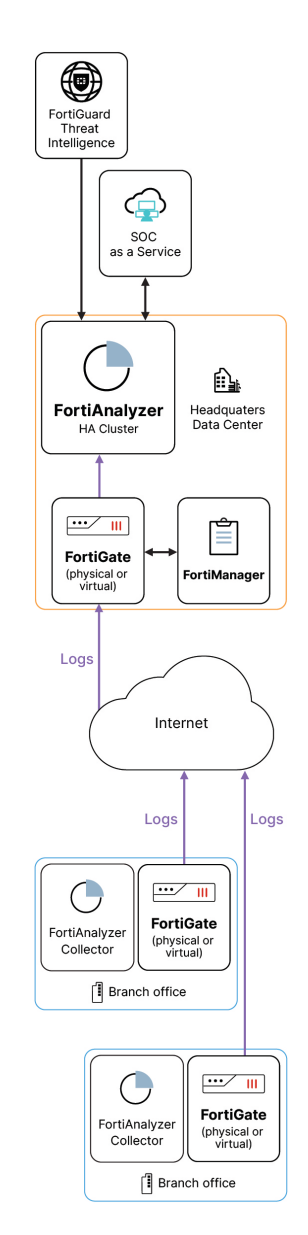
FortiAnalyzer-3510G
FortiAnalyzer-3510G Centralized log & analysis appliance - 2 x GbE RJ45 ports, 2x SFP28 ports, 96TB storage, dual power supplies, 5000 GB/Day of logs.
FortiAnalyzer-3510G Hardware plus FortiCare Premium and FortiAnalyzer Enterprise Protection
FortiAnalyzer-3510G Hardware plus 1 Year FortiCare Premium and FortiAnalyzer Enterprise Protection
FortiAnalyzer-3510G Hardware plus 3 Year FortiCare Premium and FortiAnalyzer Enterprise Protection
FortiAnalyzer-3510G Hardware plus 5 Year FortiCare Premium and FortiAnalyzer Enterprise Protection
FortiAnalyzer AI Top Up License FortiAI Assistant upgrade license for adding 500,000 AI tokens
FortiAnalyzer AI Top Up License 1 Year FortiAI Assistant upgrade license for adding 500,000 AI tokens
#FC1-10-AITAZ-1089-02-12
List Price: $100.00
Our Price: $74.43
FortiAnalyzer AI Top Up License 3 Year FortiAI Assistant upgrade license for adding 500,000 AI tokens
#FC1-10-AITAZ-1089-02-36
List Price: $300.00
Our Price: $223.28
FortiAnalyzer AI Top Up License 5 Year FortiAI Assistant upgrade license for adding 500,000 AI tokens
#FC1-10-AITAZ-1089-02-60
List Price: $500.00
Our Price: $432.90
FortiAnalyzer- Upgrade FortiCare Premium to Elite (for 1- 101 GB/Day of Logs. Require FortiCare Premium support)
FortiAnalyzer- FortiCare Upgrade from Premium to Elite 1 Year Upgrade FortiCare Premium to Elite (for 1- 101 GB/Day of Logs. Require FortiCare Premium support)
#FC5-10-LV0VM-204-02-12
List Price: $1,149.25
Our Price: $986.92
FortiAnalyzer- FortiCare Upgrade from Premium to Elite 3 Year Upgrade FortiCare Premium to Elite (for 1- 101 GB/Day of Logs. Require FortiCare Premium support)
#FC5-10-LV0VM-204-02-36
List Price: $3,447.75
Our Price: $2,960.75
FortiAnalyzer- FortiCare Upgrade from Premium to Elite 5 Year Upgrade FortiCare Premium to Elite (for 1- 101 GB/Day of Logs. Require FortiCare Premium support)
#FC5-10-LV0VM-204-02-60
List Price: $5,746.25
Our Price: $4,934.60
FortiAnalyzer- Upgrade FortiCare Premium to Elite (for 1- 2001 GB/Day of Logs. Require FortiCare Premium support)
FortiAnalyzer- FortiCare Upgrade from Premium to Elite 1 Year Upgrade FortiCare Premium to Elite (for 1- 2001 GB/Day of Logs. Require FortiCare Premium support)
#FC7-10-LV0VM-204-02-12
List Price: $5,098.00
Our Price: $4,377.91
FortiAnalyzer- FortiCare Upgrade from Premium to Elite 3 Year Upgrade FortiCare Premium to Elite (for 1- 2001 GB/Day of Logs. Require FortiCare Premium support)
#FC7-10-LV0VM-204-02-36
List Price: $15,294.00
Our Price: $13,133.72
FortiAnalyzer- FortiCare Upgrade from Premium to Elite 5 Year Upgrade FortiCare Premium to Elite (for 1- 2001 GB/Day of Logs. Require FortiCare Premium support)
FortiAnalyzer- Upgrade FortiCare Premium to Elite (for 1- 501 GB/Day of Logs. Require FortiCare Premium support)
FortiAnalyzer- FortiCare Upgrade from Premium to Elite 1 Year Upgrade FortiCare Premium to Elite (for 1- 501 GB/Day of Logs. Require FortiCare Premium support)
#FC6-10-LV0VM-204-02-12
List Price: $1,619.25
Our Price: $1,390.53
FortiAnalyzer- FortiCare Upgrade from Premium to Elite 3 Year Upgrade FortiCare Premium to Elite (for 1- 501 GB/Day of Logs. Require FortiCare Premium support)
#FC6-10-LV0VM-204-02-36
List Price: $4,857.75
Our Price: $4,171.59
FortiAnalyzer- FortiCare Upgrade from Premium to Elite 5 Year Upgrade FortiCare Premium to Elite (for 1- 501 GB/Day of Logs. Require FortiCare Premium support)
#FC6-10-LV0VM-204-02-60
List Price: $8,096.25
Our Price: $6,952.66
FortiAnalyzer-3510G Enterprise Protection (FortiCare Premium plus Indicators of Compromise Service, Security Automation Service, FortiTIP SaaS Extension, and FortiGuard Outbreak Service)
FortiAnalyzer-3510G 1 Year Enterprise Protection (FortiCare Premium plus Indicators of Compromise Service, Security Automation Service, FortiTIP SaaS Extension, and FortiGuard Outbreak Service)
FortiAnalyzer-3510G 3 Year Enterprise Protection (FortiCare Premium plus Indicators of Compromise Service, Security Automation Service, FortiTIP SaaS Extension, and FortiGuard Outbreak Service)
FortiAnalyzer-3510G 5 Year Enterprise Protection (FortiCare Premium plus Indicators of Compromise Service, Security Automation Service, FortiTIP SaaS Extension, and FortiGuard Outbreak Service)
FortiAnalyzer-3510G FortiAnalyzer Attack Surface Security Rating and Compliance
FortiAnalyzer-3510G 1 Year FortiAnalyzer Attack Surface Security Rating and Compliance
FortiAnalyzer-3510G 3 Year FortiAnalyzer Attack Surface Security Rating and Compliance
FortiAnalyzer-3510G 5 Year FortiAnalyzer Attack Surface Security Rating and Compliance
FortiAnalyzer-3510G FortiAnalyzer Security Automation Service including premium reports, event handlers, SIEM correlation rules for advanced threat detection and SOAR playbooks
FortiAnalyzer-3510G 1 Year FortiAnalyzer Security Automation Service including premium reports, event handlers, SIEM correlation rules for advanced threat detection and SOAR playbooks
FortiAnalyzer-3510G 3 Year FortiAnalyzer Security Automation Service including premium reports, event handlers, SIEM correlation rules for advanced threat detection and SOAR playbooks
FortiAnalyzer-3510G 5 Year FortiAnalyzer Security Automation Service including premium reports, event handlers, SIEM correlation rules for advanced threat detection and SOAR playbooks
FortiAnalyzer-3510G FortiCare Elite Support
FortiAnalyzer-3510G 1 Year FortiCare Elite Support
FortiAnalyzer-3510G 3 Year FortiCare Elite Support
FortiAnalyzer-3510G 5 Year FortiCare Elite Support
FortiAnalyzer-3510G FortiCare Premium Support
FortiAnalyzer-3510G 1 Year FortiCare Premium Support
FortiAnalyzer-3510G 3 Year FortiCare Premium Support
FortiAnalyzer-3510G 5 Year FortiCare Premium Support
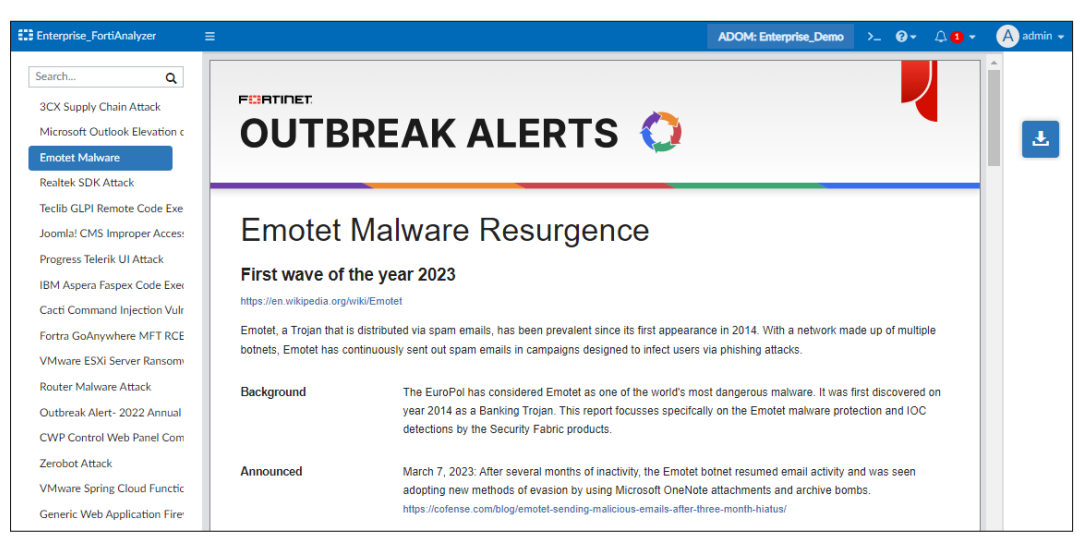
FortiAnalyzer-3510G FortiGuard IOC and Outbreak Detection Service
FortiAnalyzer-3510G 1 Year FortiGuard IOC and Outbreak Detection Service
FortiAnalyzer-3510G 3 Year FortiGuard IOC and Outbreak Detection Service
FortiAnalyzer-3510G 5 Year FortiGuard IOC and Outbreak Detection Service
FortiAnalyzer-3510G FortiGuard Threat Intel Platform (TIP) SaaS Service Extension
FortiAnalyzer-3510G 1 Year FortiGuard Threat Intel Platform (TIP) SaaS Service Extension
FortiAnalyzer-3510G 3 Year FortiGuard Threat Intel Platform (TIP) SaaS Service Extension
FortiAnalyzer-3510G 5 Year FortiGuard Threat Intel Platform (TIP) SaaS Service Extension
FortiAnalyzer-3510G OT Security Service including advanced OT analytics, risk and compliance reports, event handlers, and use-case correlation rules
FortiAnalyzer-3510G 1 Year OT Security Service including advanced OT analytics, risk and compliance reports, event handlers, and use-case correlation rules
FortiAnalyzer-3510G 3 Year OT Security Service including advanced OT analytics, risk and compliance reports, event handlers, and use-case correlation rules
FortiAnalyzer-3510G 5 Year OT Security Service including advanced OT analytics, risk and compliance reports, event handlers, and use-case correlation rules
FortiAnalyzer-3510G Upgrade FortiCare Premium to Elite (Require FortiCare Premium)
FortiAnalyzer-3510G 1 Year Upgrade FortiCare Premium to Elite (Require FortiCare Premium)
#FC-10-AZ3AG-204-02-12
List Price: $7,183.60
Our Price: $6,168.92
FortiAnalyzer-3510G 3 Year Upgrade FortiCare Premium to Elite (Require FortiCare Premium)
FortiAnalyzer-3510G 5 Year Upgrade FortiCare Premium to Elite (Require FortiCare Premium)
FortiAnalyzer-3510G 24x7 SOCaaS expert-delivered monitoring and management service
FortiAnalyzer-3510G 1 Year 24x7 SOCaaS expert-delivered monitoring and management service
FortiAnalyzer-3510G 3 Year 24x7 SOCaaS expert-delivered monitoring and management service
FortiAnalyzer-3510G 5 Year 24x7 SOCaaS expert-delivered monitoring and management service