Fortinet FortiDeceptor - Deception Platform
FortiDeceptor provides early detection and isolation of sophisticated human and automated attacks by deceiving attackers into revealing themselves


FortiDeceptor Hardware Appliances
FortiDeceptor Virtual Machines
Overview
FortiDeceptor, part of Fortinet SecOps Platform, detects and responds to in-network attacks such as stolen credential usage, lateral movement, man-in-the-middle, and ransomware. Adding FortiDeceptor as part of your cybersecurity strategy helps shift your defenses from reactive to proactive with intrusion-based detection layered with contextual intelligence.
Early, accurate attack detection (no false positives) reduces attacker’s dwell time
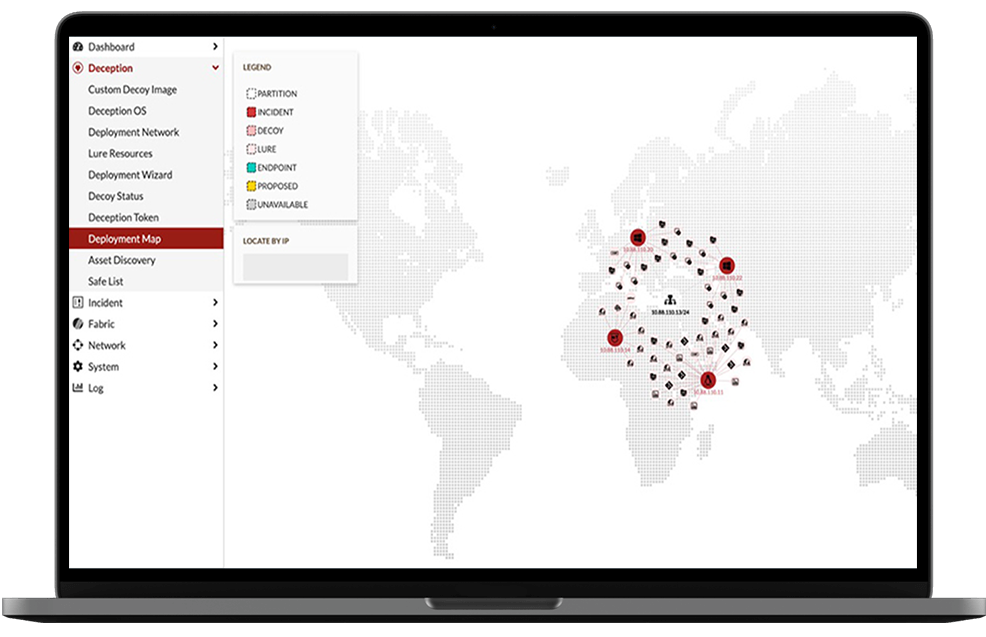
FortiDeceptor lures attackers FortiDeceptor-as-a-Service, a SaaS-based deception solution, detects and responds to in-network attacks, such as stolen credential usage, lateral movement, man-in-the-middle (MITM), and ransomware. Using an organization’s available IP addresses, decoys run in the FortiDeceptor-as-a-Service platform residing in the Fortinet private cloud. Decoys leverage only unused IP addresses, and do not impact network availability. When an automated/human attacker engages with a decoy, they are already outside your network, and cannot cause any further damage. revealing themselves early at the reconnaissance stage by engaging with a wide range of deception assets distributed throughout your environment. The platform generates high-fidelity alerts based on real-time engagement with attackers and malware, providing attack activity analysis and attack isolation. This helps alleviate the burden on SOC teams inundated with false-positive alerts. FortiDeceptor also correlates incident and campaign activities and collects IOCs and TTPs, allowing SOC teams to make smarter, faster decisions.
Watch the VideoDivert attacks outside your network and keep it safe with FortiDeceptor-as-a-Service
FortiDeceptor-as-a-Service, a SaaS-based deception solution, detects and responds to in-network attacks, such as stolen credential usage, lateral movement, man-in-the-middle (MITM), and ransomware. Using an organization’s available IP addresses, decoys run in the FortiDeceptor-as-a-Service platform residing in the Fortinet private cloud. Decoys leverage only unused IP addresses, and do not impact network availability. When an automated/human attacker engages with a decoy, they are already outside your network, and cannot cause any further damage.
Download Solution Brief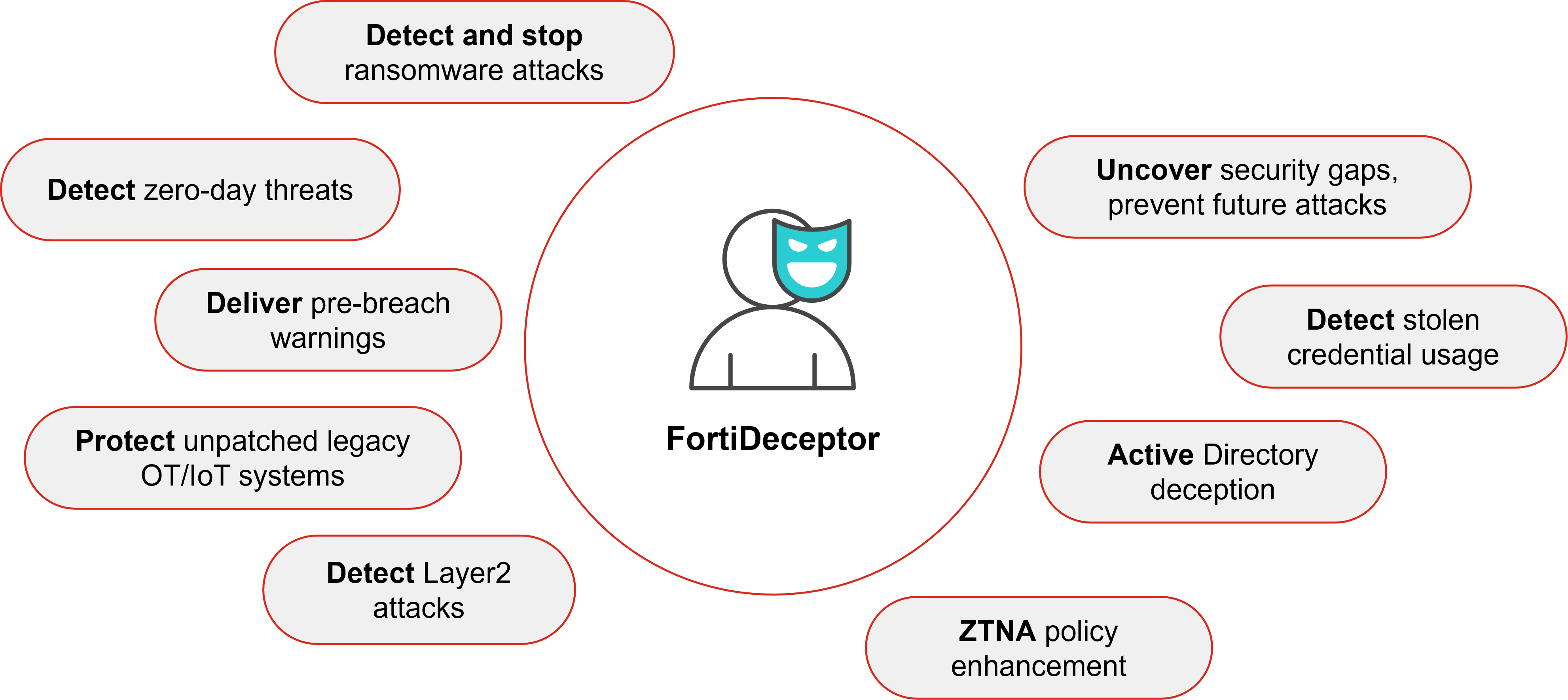
Automatically contain in-network attacks before they spread
When an attacker engages with deception assets, for example, fake files on an endpoint, or if malware tries to encrypt fake file, FortiDeceptor can neutralize the attack by automatically isolating any compromised endpoint. This prevents the attack from spreading and stops communication with a C&C server. This can be done using FortiDeceptor’s built-in, automated attack quarantine capabilities or by sending an alert to SIEM/SOAR for an orchestrated response.
Watch the VideoScale up dynamic protection as the threat level increases
To combat emerging threats and vulnerabilities, FortiDeceptor enables on-demand creation of deception decoys based on newly discovered vulnerabilities or suspicious activity, providing automated, dynamic protection across OT/IoT/IT environments. Further, FortiDeceptor response capabilities go beyond SOAR evidence enrichment and automated host quarantine playbooks, by providing a SOAR playbook for on-demand deployment of deception assets in response to suspicious activity in your network.
Features and Benefits
Dynamic deception platform, with extensive support for IT/OT/IoT environments, diverts attackers from sensitive assets to shift the balance to the defender’s advantage.
![]()
Visibility & Accelerated Response
Integrates with Fortinet Security Fabric and third-party security controls (SIEM, SOAR, EDR, sandbox)
![]()
Insider Threat Detection
Reduces dwell time and false positives, detects early recon & lateral movement to misdirect attacks
![]()
Forensics & Threat Intelligence
Captures and analyzes attack activities in real time, provides detailed forensics, collects IOCs & TTPs
![]()
Quarantined/Unquarantined Attacks
Infected endpoints can be quarantined away from the production network
![]()
Optimized for OT/IoT Networks
Extensive decoys include SCADA systems, IoT sensors, plus you can upload your own decoys
![]()
Easy Deployment & Maintenance
Asset-match decoys are automatically deployed with no impact on stability and performance
Use Cases
Dynamic Deception
Network visibility and breach detection via passive footprint. Detects threats to assets that cannot provide their own telemetry.
Ransomware Mitigation
Early detection and response to ransomware attacks. Misleads malware to encrypt fake files, triggering automatic blocking of the infected endpoint.
Lateral Movement Detection
Detects attackers early in the discovery phase and misdirects lateral activities to the decoy and away from real assets.
Active Directory Deception
Network visibility and breach detection via passive footprint. Detects threats to assets that cannot provide their own telemetry.
Security for IT/OT/IOT/IOMT
Extensive decoys including SCADA systems, IoT sensors are available, plus the ability to upload your own decoys.
Layer 2 Attack Detection
Detects MITM attacks, NBNSSpoofSpotter, NBT-NS, mDNS, LLMNR spoofing, using both active and passive methods.




