Overview:
FortiAuthenticator FSSO Features:
- Enables identity and role-based security policies in the Fortinet secured enterprise network without the need for additional authentication through integration with Active Directory
- Strengthens enterprise security by simplifying and centralizing the management of user identity information
Additional FortiAuthenticator Features:
- Secure Two-factor / OTP Authentication with full support for FortiToken
- RADIUS and LDAP Authentication
- Certificate management for enterprise VPN deployment
- IEEE802.1X support for wired and wireless network security
FortiAuthenticator user identity management appliances strengthen enterprise security by simplifying and centralizing the management and storage of user identity information.
Enterprise Network Identity Policy
Network and Internet access is key for almost every role within the enterprise; however, this requirement must be balanced with the risk that it brings. The key objective of every enterprise is to provide secure but controlled network access enabling the right person the right access at the right time, without compromising on security.
Fortinet Single Sign-On is the method of providing secure identity and role-based access to the Fortinet connected network. Through integration with existing Active Directory or LDAP authentication systems, it enables enterprise user identity based security without impeding the user or generating work for network administrators. FortiAuthenticator builds on the foundations of Fortinet Single Sign-on, adding a greater range of user identification methods and greater scalability. FortiAuthenticator is the gatekeeper of authorization into the Fortinet secured enterprise network identifying users, querying access permissions from third party systems and communicating this information to FortiGate devices for use in Identity-Based Policies.
FortiAuthenticator delivers transparent identification via a wide range of methods:
- Polling of an Active Directory Domain Controller;
- Integration with FortiAuthenticator Single Sign-On Mobility Agent which detects login, IP address changes and logout;
- FSSO Portal based authentication with tracking widgets to reduce the need for repeated authentications;
- Monitoring of RADIUS Accounting Start records.
Features & Benefits:
| FSSO Transparent User Identification |
Zero impact for enterprise users. |
| Integration with LDAP and AD for group membership |
Utilizes existing systems for network authorization information, reducing deployment times and streamlining management processes. Integration with existing procedures for user management. |
| Wide range of user identification methods |
Flexible user identification methods for integration with the most diverse of enterprise environments. |
| Enablement of identity and role-based security |
Allows security administrator to give users access to the relevant network and application resources appropriate to their role. while retaining control and minimizing risk. |
| RADIUS and LDAP User Authentication |
Local Authentication database with RADIUS and LDAP interfaces centralizes user management. |
| Wide Range of Strong Authentication Methods |
Strong authentication provided by FortiAuthenticator via hardware tokens, e-mail, SMS, e-mail and digital certificates help to enhance password security and mitigate the risk of password disclosure, replay or brute forcing. |
| User Self-registration and Password Recovery |
Reduces the need for administrator intervention by allowing the user to perform their own registration and resolve their own password issues, which also improves user satisfaction. |
| Integration with Active Directory and LDAP |
Integration with existing directory simplifies deployment, speeds up installation times and reutilizes existing development. |
| Certificate Management |
Streamlined certificate management enables rapid, cost-effective deployment of certificate-based authentication methods such as VPN. |
| 802.1X Authentication |
Deliver enterprise port access control to validate users connection to the LAN and Wireless LAN to prevent unauthorized access to the network. |
Highlights:
FortiAuthenticator Single Sign-On User Identification Methods
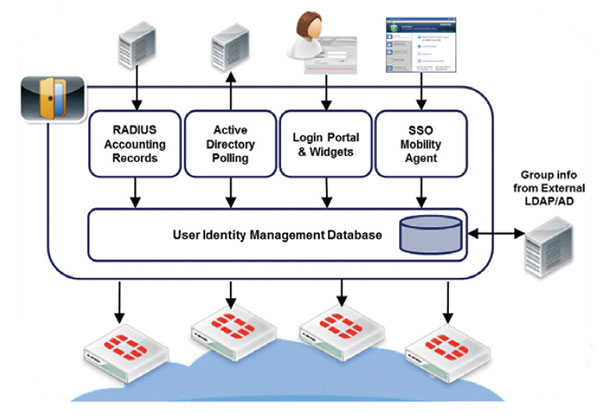
FortiAuthenticator can identify users through a varied range of methods and integrate with third party LDAP or Active Directory systems to apply group or role data to the user and communicate with FortiGate for use in Identity based policies. FortiAuthenticator is completely flexible and can utilize these methods in combination. For example, in a large enterprise, AD polling or FortiAuthenticator SSO Mobility Agent may be chosen as the primary method for transparent authentication with fallback to the portal for non-domain systems or 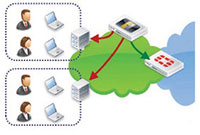 guest users.
guest users.
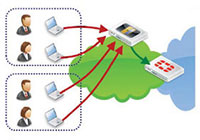
Active Directory Polling
User authentication into active directory is detected by regularly polling domain controllers. When a user login is detected, the username, IP and group details are entered into the FortiAuthenticator User Identity Management Database and according to the local policy, can be shared with multiple FortiGate devices.
 FortiAuthenticator SSO Mobility Agent
FortiAuthenticator SSO Mobility Agent
For complicated distributed domain architectures where polling of domain controllers is not feasible or desired, an alternative is the FortiAuthenticator SSO Client. Distributed as part of FortiClient or as a standalone installation for Windows PCs, the client communicates login, IP stack changes (Wired > Wireless, wireless network roaming) and logout events to the FortiAuthenticator, removing the need for polling methods.
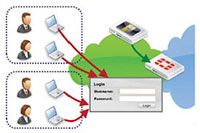 FortiAuthenticator Portal and Widgets
FortiAuthenticator Portal and Widgets
For systems which do not support AD polling or where a client is not feasible, FortiAuthenticator provides an explicit authentication portal. This allows the users to manually authenticate to the FortiAuthenticator and subsequently into the network. To minimize the impact of repeated logins required for manual authentication, a set of widgets is provided for embedding into an organization's intranet which automatically logs the users in through the use of browser cookies whenever they access the intranet homepage.
 RADIUS Accounting Login
RADIUS Accounting Login
In a network which utilizes RADIUS authentication (e.g. wireless or VPN authentication), RADIUS Accounting can be used as a user identification method. This information is used to trigger user login and to provide IP and group information, removing the need for a second tier of authentication.
Additional Functionality
Strong User Identity with Two-factor Authentication
FortiAuthenticator extends two-factor authentication capability to multiple FortiGate appliances and to third party solutions that support RADIUS or LDAP authentication. User identity information from FortiAuthenticator combined with authentication information from FortiToken ensures that only authorized individuals are granted access to your organization's sensitive information. This additional layer of security greatly reduces the possibility of data leaks while helping companies meet audit requirements associated with government and business privacy regulations. FortiAuthenticator supports the widest range of tokens possible to suit your user requirements. With the physical time based FortiToken-200, FortiToken Mobile (for iOS and Android), e-mail and SMS tokens, FortiAuthenticator has a token options for all users and scenarios. Two-factor authentication can be used to control access to applications such as FortiGate management, SSL and IPSEC VPN, Wireless Captive Portal login and third party, RADIUS compliant networking equipment.
To streamline local user management, FortiAuthenticator includes user self-registration and password recovery features.
Enterprise Certificate Based VPNs
Site-to-site VPNs often provide access direct to the heart of the enterprise network from many remote locations. Often these VPNs are secured simply by a preshared key, which, if compromised, could give access to the whole network. FortiOS support certificate-based VPNs; however, use of certificate secured VPNs has been limited, primarily due to the overhead and complexity introduced by certificate management. FortiAuthenticator removes this overhead involved by streamlining the bulk deployment of certificates for VPN use in a FortiGate environment by cooperating with FortiManager for the configuration and automating the secure certificate delivery via the SCEP protocol.
For client-based certificate VPNs, certificates can be created and stored on the FortiToken300 USB Certificate store. This secure, pin protected certificate store is compatible with FortiClient and can be used to enhance the security of client VPN connections in conjunction with FortiAuthenticator.





 guest users.
guest users. FortiAuthenticator SSO Mobility Agent
FortiAuthenticator SSO Mobility Agent FortiAuthenticator Portal and Widgets
FortiAuthenticator Portal and Widgets RADIUS Accounting Login
RADIUS Accounting Login

